
MDR Security Operation Service Stop threats with an elite, AI-powered response team

Adlumin MDR delivers an AI-powered, expert-led SOC that hunts, detects, and neutralizes attacks while continuously strengthening your security posture.
Transform threats into predictable cyber resilience
Meet the adaptive security operations service ready to tame cyberattacks for you, from proactive threat hunting and breach prevention to lightning-fast response and containment.
Overcome cybersecurity challenges with an enterprise-grade SOC built for businesses of all sizes
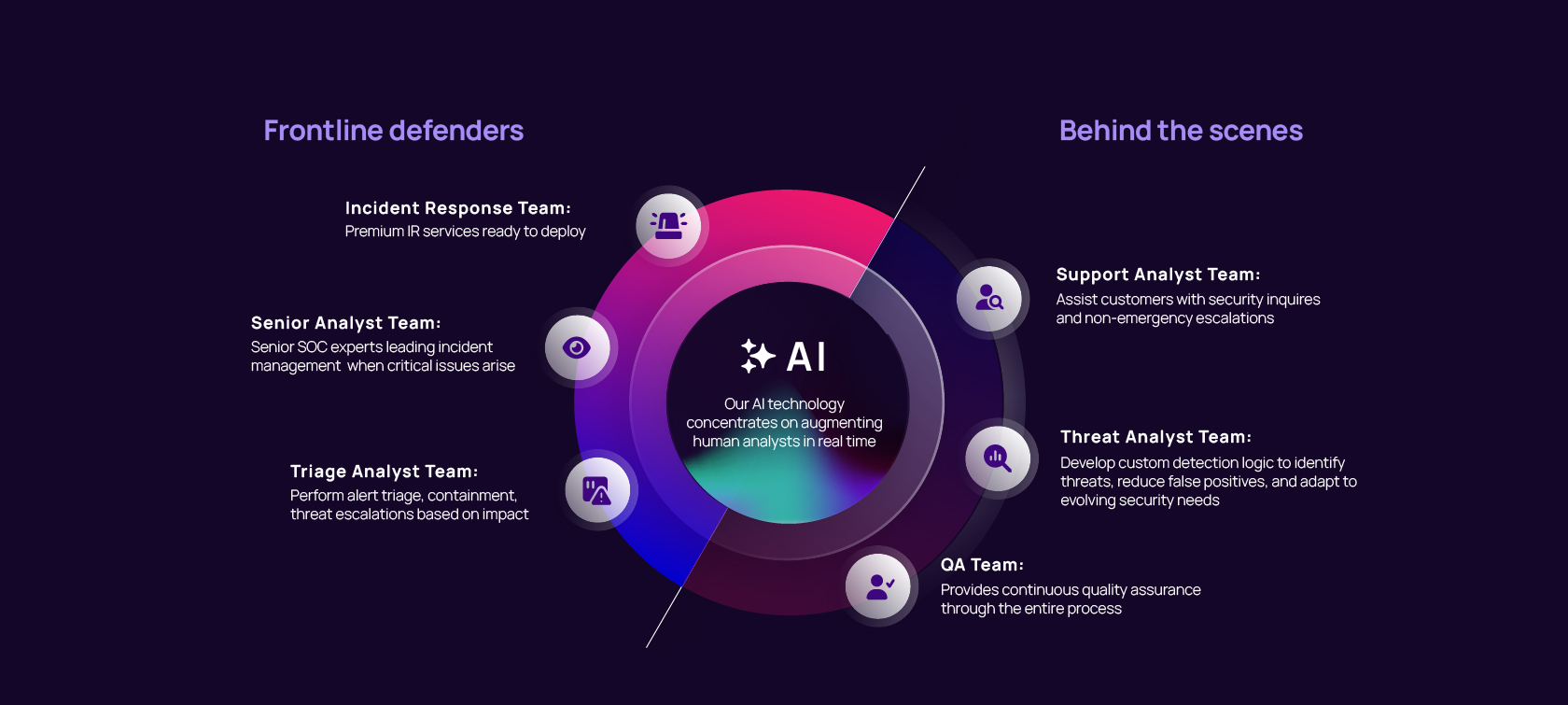
AI-powered. Human-led.
Our SOC combines the efficiency of AI with a team of always-on experts ready to deliver faster responses, better outcomes, and continuous security improvements.
The MDR solution packed
with more capabilities
Adlumin MDR is layered over our full-featured Adlumin XDR, with built-in SOAR, SIEM,
and UEBA capabilities, saving you the overhead of piecing together pricey
third-party add-ons for log management, behavioral analytics, or automated response.

SIEM
(Security Information and Event Management)
SOAR
(Security Orchestration, Automation, and Response)

UEBA
(User and Entity Behavior Analytics)
Vendor agnostic flexibility and control
Our MDR service monitors across your existing tool set so you can tailor the tech stack that works best for your team.
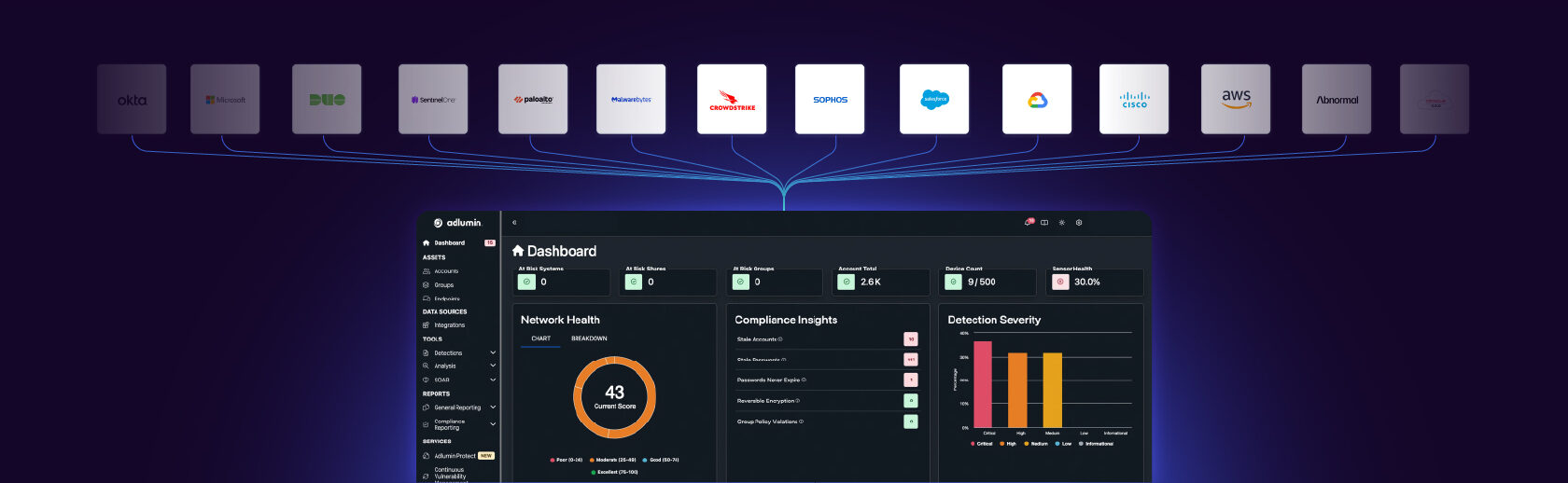
Meet the XDR that powers it all
Adlumin MDR is an elite SOC, but what fuels that engine? It’s our adaptive XDR platform that leverages proprietary AI to drive better security outcomes.

Managed Detection and Response packages
| Microsoft 365 Breach | MDR Standard | MDR Advanced | |
|---|---|---|---|
| Data | |||
| Data Retention | 30 days | 30 days | 90 days |
| Sources | |||
| Adlumin Endpoint Agent | - | ||
| API Integrations | Microsoft 365 only | ||
| Adlumin VM Collector for non-API Data Ingestion (ex. Syslog) |
- | - | |
| Capabilities | |||
| Darknet Monitoring* | - | ||
| Cyber Threat Intelligence | |||
| SIEM | Limited to Microsoft data | ||
| Vulnerability Scanning | - | ||
| Network Insights | - | ||
| Reporting and Compliance | |||
| UEBA | |||
| Honeypots | - | - | |
| SOAR | Identity only |
* Darknet Monitoring not applicable for educational institutions
Adlumin Protect Warranty
Safeguard against business continuity and insurance loss up to $500,000 reimbursement. The Adlumin Protect Warranty is included with our Adlumin Protection Plus suite at no additional cost .
We were alerted the CEO of our large healthcare client had fallen victim to an email compromise. We were able to immediately secure the account. Adlumin is a game changer.
Zane Patalive Real IT Care
Resources
Talk with a specialist to learn more about Adlumin MDR
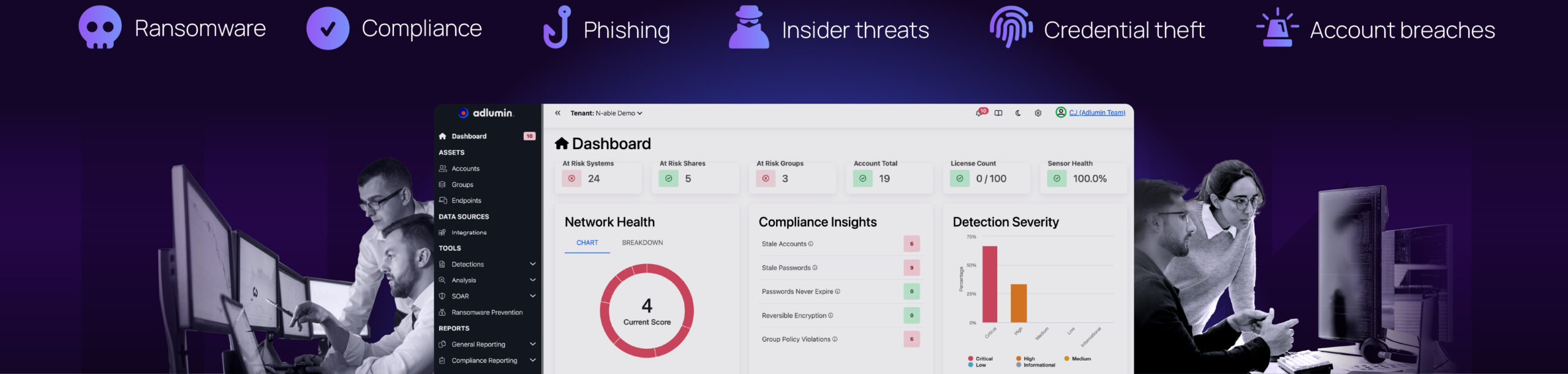
See how the speed, visibility, and contextual insights of Adlumin MDR illuminate your security operations.
- AI Threat Detection: Spot and stop risks in real time with AI.
- Automated Response: Use playbooks to speed up your containment and resolution.
- Effortless Compliance: Get instant visibility into your PCI DSS, HIPAA, and other standards.
- Executive Dashboards: View insights tailored for you, your CSOs, and your board.
- MDR Collaboration: See what you’re investigating and how your threats are being resolved.







